Standalone Access Control
- Technogroups
- Standalone Access Control

-
+
Happy Clients
-
+
Associate Business Partners
-
years+
Business Experience
Standalone access control systems
Standalone access control systems provide a simple and cost-effective solution for securing entry points without the need for a centralized network. These systems typically utilize devices such as keypads, card readers, or biometric scanners, allowing users to manage access independently. Their ease of installation and operation makes them ideal for small businesses, residential properties, and remote locations where a full-scale security system may not be necessary.


Pin Access in Standalone access control
Users can gain access by entering a predetermined Personal Identification Number (PIN) on a keypad. This method is straightforward and allows for easy changes to access codes as needed.
Easy management: They can be easily issued, deactivated, or reissued as needed.
Versatile use: They can be used at various access points, including entrances, gates, and elevators.

Biometric Access Control
Biometric access control systems offer a highly secure and convenient way to manage access to residential properties. By utilizing unique physical characteristics such as fingerprints, facial recognition, or iris scans, these systems can effectively verify the identity of individuals and grant or deny access accordingly. This eliminates the risks associated with lost or stolen keys or cards, providing a significant boost to security.
Benefits of Biometric Access
Enhanced security
Reduced risk of unauthorized access
Increased convenience
Improved accountability
Mobile App Access in Standalone Access Control
Accessing standalone access control systems through mobile phones offers a convenient way to manage entry points. Users can unlock doors, grant access, and monitor activity directly from a dedicated app, allowing for remote management without needing to be physically present. This functionality streamlines the process of managing access permissions, making it ideal for busy environments.
In addition to convenience, mobile access enhances security with features like encryption and real-time notifications. Users can easily generate or revoke access codes and receive alerts about access events, ensuring they stay informed about who enters their premises. This integration of mobile technology not only simplifies security management but also provides a user-friendly experience tailored to modern needs.
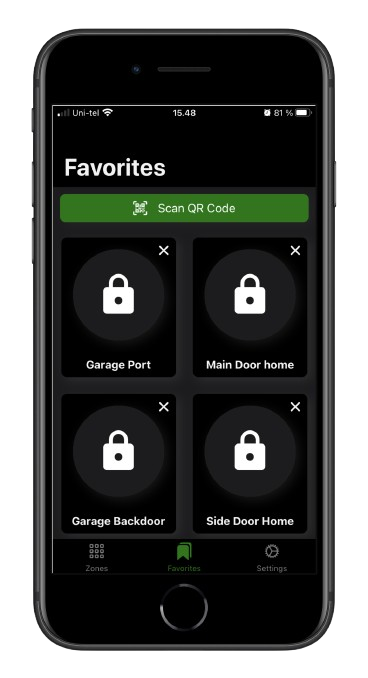
benefits of mobile app access control
Real-Time Monitoring
Convenience
Easy User Management
Enhanced security
Mobile access for standalone access control systems offers significant benefits, including convenience and real-time monitoring, allowing users to manage entry points remotely. It simplifies user management by enabling quick adjustments to access permissions and enhances security through features like encryption and two-factor authentication.
Business Of Growth
We businesss standard chunk of Ipsum used since is Agency & Star tup.
We Grow Business
We businesss standard chunk of Ipsum used since is Agency & Star tup.
Markting Solution
We businesss standard chunk of Ipsum used since is Agency & Star tup.


