Interlocking Door Access
- Technogroups
- Interlocking Door Access

-
+
Happy Clients
-
+
Associate Business Partners
-
years+
Business Experience
Interlocking Door Access Control: A Comprehensive Security Solution
Interlocking door access control systems enhance security by ensuring that one door can only open when another door is securely closed, effectively preventing unauthorized access and tailgating. Commonly used in high-security environments such as data centers and laboratories, these systems can integrate various access control methods, including card readers and biometric scanners. By controlling the flow of individuals in and out of sensitive areas, interlocking doors not only improve security but also provide real-time monitoring and auditing capabilities, making them an essential component of modern security strategies.
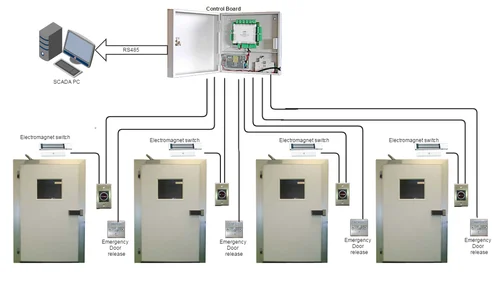

Accessing Interlocking Doors Using Card Access Control
Accessing interlocking doors using card access control involves the use of RFID cards, smart cards, or key fobs to authenticate users before granting entry. In this system, each interlocking door is equipped with a card reader that verifies the credentials of the individual attempting to enter. When a user presents their card to the reader at the first door, the system checks the card's validity against a database of authorized users.
Easy management: They can be easily issued, deactivated, or reissued as needed.
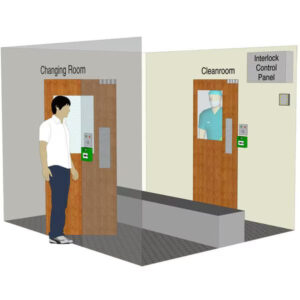
Biometric Access Control
Accessing interlocking door control systems using biometric authentication provides a highly secure method for managing entry to restricted areas. Biometric systems utilize unique physical characteristics, such as fingerprints, facial recognition, or iris scans, to verify the identity of individuals before granting access.
Benefits of Biometric Access
High Security
Interlocking Mechanism
User Convenience
Enhanced Security
Mobile App Access in Interlocking door Access Control
Interlocking door access control systems can be effectively managed through mobile applications, providing a seamless and secure way for users to gain entry to restricted areas. With this technology, users can unlock interlocking doors directly from their smartphones, enhancing convenience while maintaining high security.
In addition to convenience, mobile access enhances security with features like encryption and real-time notifications. Users can easily generate or revoke access codes and receive alerts about access events, ensuring they stay informed about who enters their premises. This integration of mobile technology not only simplifies security management but also provides a user-friendly experience tailored to modern needs.
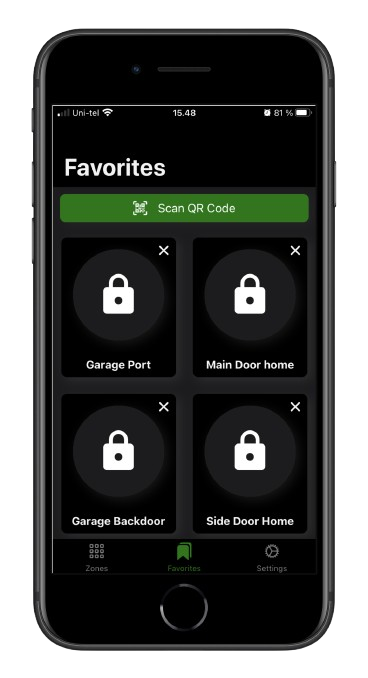
benefits of mobile app access control
Remote Access Control
Enhanced Security
Real-Time Monitoring
User Convenience
By integrating mobile app technology with interlocking door access control, organizations can enhance security, streamline access management, and provide a more convenient experience for users. This modern approach to access control is particularly beneficial in high-security environments, such as data centers, laboratories, and secure facilities.
Business Of Growth
We businesss standard chunk of Ipsum used since is Agency & Star tup.
We Grow Business
We businesss standard chunk of Ipsum used since is Agency & Star tup.
Markting Solution
We businesss standard chunk of Ipsum used since is Agency & Star tup.


