Welcome To KS TechnoGroup!
Commercial Access Control Systems
Anywhere In the World 24 x7!
Commercial Access Control Systems
Commercial access control systems and devices provide a secure and efficient way to manage access to buildings and facilities. They are essential for businesses, schools, and other organizations that need to control who can enter and exit their premises.
- Access control panels: These are the central control units that manage the entire system. They receive signals from readers, process them, and send commands to locks and other devices.
- Readers: Readers are used to scan credentials, such as cards, fobs, or biometric data, and send the information to the access control panel.
- Credentials: Credentials are the physical or digital objects that individuals use to gain access. They can be cards, fobs, mobile phones, or even biometric data like fingerprints or facial recognition.
- Locks: Locks are the devices that control access to doors and gates. They can be electromechanical, magnetic, or biometric.
- Software: Access control software provides a user interface for managing the system. It allows administrators to create user profiles, assign access rights, monitor activity, and generate reports.


Card-Based Access Control Systems
Card-based access control systems are one of the most widely used and trusted methods for securing buildings and facilities. These systems rely on plastic cards with magnetic stripes or embedded chips to verify the identity of individuals seeking access.
- Credential Issuance: Each authorized person is issued a unique card containing a specific identification code.
- Access Point: At the entry point, a card reader is installed.
- Verification: When an individual presents their card to the reader, the system verifies the card’s authenticity and checks if the associated user is authorized to access the area.
- Access Granted or Denied: Based on the verification results, the system either grants or denies access. If granted, the door or gate is opened.

Biometric Access Control Systems: A Touch of Security
Biometric access control systems use unique physical characteristics to verify the identity of individuals, providing a highly secure and convenient way to manage access to facilities. These systems eliminate the need for physical keys or cards, reducing the risk of lost or stolen credentials.
Types of biometric systems:
Fingerprint recognition: This is one of the most common biometric technologies, using the unique patterns on a person's fingers for identification.
Facial recognition: This system analyzes facial features to identify individuals.
Iris recognition: This technology scans the unique patterns in a person's iris, the colored part of the eye.
Hand geometry: This system measures the unique dimensions and features of a person's hand.
Mobile Access Control Systems: A Convenient and Secure Solution
Mobile access control systems (MACS) have gained significant popularity in recent years, offering a convenient and secure way to manage access to buildings and facilities. By leveraging smartphones as credentials, MACS eliminate the need for physical cards or fobs, providing a streamlined and user-friendly experience.
- App Installation: Users download and install a dedicated mobile app on their smartphones.
- Credential Enrollment: Users enroll their smartphones as credentials by following the app’s instructions. This process may involve biometric authentication or the use of unique codes.
- Access Control: At the entry point, a reader is installed that can communicate with the app via Bluetooth, NFC, or QR codes.
- Verification: When a user approaches the reader with their smartphone, the app verifies their credentials and grants or denies access based on their authorization level.
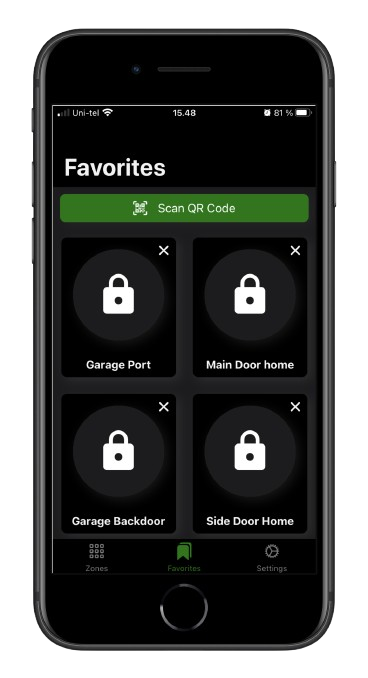
benefits of mobile app access control
Convenience: Users can easily carry their smartphones with them, eliminating the need for physical keys or cards.
Security: Biometric authentication and encryption can enhance the security of mobile access systems, reducing the risk of unauthorized access.
Flexibility: MACS can be easily integrated with other security systems, such as surveillance cameras and alarms.
User-friendly: The app-based interface provides a familiar and intuitive user experience.
While mobile app access control offers many advantages, it’s important to note that residents may need a reliable internet connection or cellular data for the app to function properly. Additionally, there may be potential security risks if the app is not properly designed or maintained.
Keypad Access Control Systems:
A Simple and Reliable Solution
Keypad access control systems are a straightforward and cost-effective method for securing buildings and facilities. These systems require users to enter a unique personal identification number (PIN) to gain access.
- PIN Assignment: Each authorized user is assigned a unique PIN code.
- Access Point: A keypad is installed at the entry point.
- PIN Entry: Users enter their PIN code on the keypad.
- Verification: The system verifies the entered PIN against the stored database.
- Access Granted or Denied: If the PIN is correct, access is granted; otherwise, it is denied.
keypad access control systems provide a basic and reliable solution for securing buildings and facilities.

Business Of Growth
We businesss standard chunk of Ipsum used since is Agency & Star tup.
We Grow Business
We businesss standard chunk of Ipsum used since is Agency & Star tup.
Markting Solution
We businesss standard chunk of Ipsum used since is Agency & Star tup.


